
DATA PROTECTION
NEUTRALISING THE IMPACT OF DATA BREACH

NEUTRALISING THE IMPACT OF DATA BREACH
By seamlessly encrypting data at source, the impact of data breach is neutralised by ensuring that information becomes unusable the moment it is removed. This means that data can be moved or copied to any other location without compromising its security. Even newly generated data such as a database export is inherently secured.
This takes place in the background so that neither the authorised user nor any application knows that encryption activities are going on. Legacy, current and new applications, and databases all benefit from this 100% encryption service without needing any change and without suffering any noticeable performance impact.
It should have always been this way.



The SPARK team consistently goes above and beyond in their scope of responsibility to service our needs. On many occasions, they provided their expert assistance designing solutions for pipeline opportunities, and troubleshooting outage risks and operational issues on our services alongside our internal experts. They intimately understand our business needs and not just meet, but exceed our expectations whilst retaining a focus on low cost service delivery. I have no hesitation in recommending SPARK to any prospective clients.
Neville Howard
Interactive | National Procurement Manager
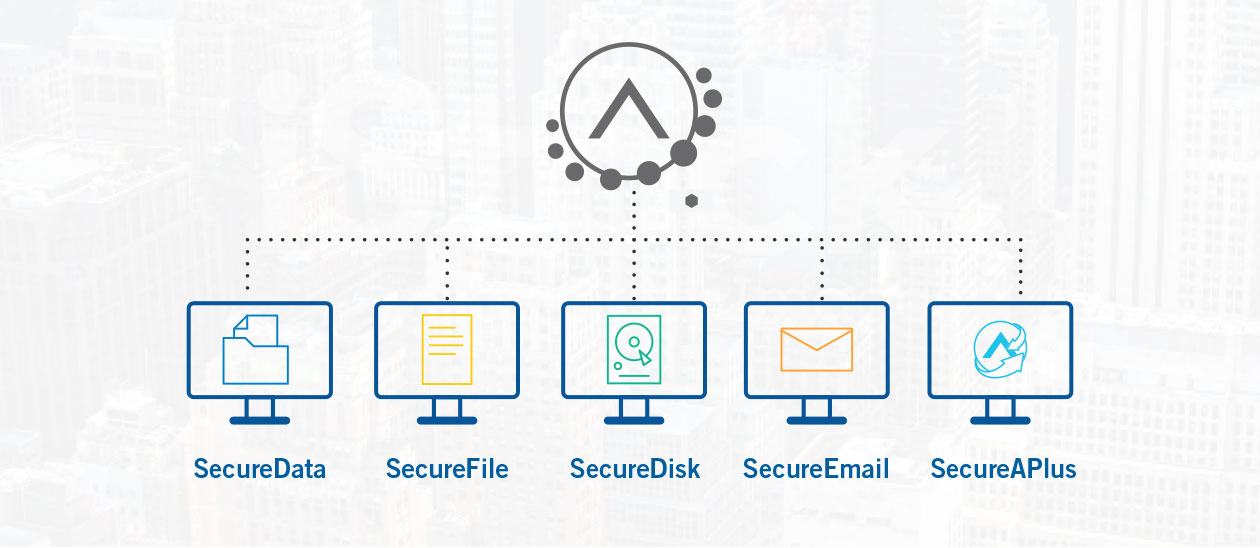
SecureAge SecureData runs as an invisible endpoint agent that automatically encrypts all user files without user deliberation, action, or even awareness. Employing a seamless PKI implementation, the persistent encryption individualizes and protects each file, whether in use, stored, lost, or stolen.
The individualized encryption of SecureData persists when any file is moved across different storage media, network locations, or, depending on company policy, even when attached to email or stored in the cloud. And using public key infrastructure (PKI), files can be shared for collaboration and access
Going beyond most file encryption tools, SecureFile provides comprehensive PKI-based document security for select files through encrypting and/or digital signing for compliance or file sharing. SecureFile generates an encrypted or signed copy of a selected file, leaving the original intact.
Most critically, the PKI features of SecureAge allows for the choice of one or more recipients of the SecureFile. From among a list of users for whom public keys exist, the creator of a SecureFile simply selects those to whom a copy of the SecureFile will be shared. Unlike SecureData, which allows for collaboration on a single file in a central location, SecureFile produces local copies for each recipient.
SecureDisk creates and manages virtual disk volumes on any Windows-based endpoint or server. All files stored in a single SecureDisk volume are encrypted together and entirely hidden from view. The same benefits of Full Disk Encryption (FDE) or similar come with SecureDisk, as well as the added flexibility of creating one or more volumes at any size chosen by the user and storing it anywhere.
The creation of SecureDisk volumes merely requires deciding upon a size, a name, and a preferred storage location. Once created and mounted, files up to the size limit of the SecureDisk volume can be dragged inside before unmounting, thereafter being invisible and inaccessible to anyone without the key. The volumes may be stored on and retrieved from any media, network drive, or the cloud.
SecureEmail ensures authenticity and privacy without requiring any training or changing the way you send and receive email.
Offering standard PKI features along with unique digital rights management (DRM) options, SecureEmail combines the industry’s best encryption technologies for compatibility with invisible, non-intrusive key management. SecureEmail plugs right into the industry-leading mail client software Microsoft Outlook and IBM Notes, offering drop-down menus for labeling and classifying email. Those user-defined classifications can be linked to security levels, such as sign and encrypt and DRM options that allow for control of messages on the recipient side when both users have SecureEmail.
First Pillar
When close to a million pieces of malware are created each day, chances are that an anti-virus is not going to keep up. The latest and most advanced forms of malware are undetectable with zero-day threats always a step ahead of any anti-virus available in the market.
Application Whitelisting puts you ahead of the curve. It strictly prevents unauthorized applications from running amok your endpoints – keeping untrusted and potentially malware-ridden software from distracting users from the things that matter to your business the most.
Second Pillar
SecureAge APEX Engine harnesses the power of artificial intelligence (AI) with deep learning to take on the threats of today and tomorrow.
Leveraging on the power of big data, the APEX engine goes beyond traditional scanners by effectively and reliably spotting malicious patterns to efficiently allow for quick decisions based on prior experience. It can adaptively update its knowledge against newer and unseen malware variants that may attempt to infect endpoints during an outbreak.
Third Pillar
The 2 key flaws of anti-viruses are that not a single one can detect close to every threat and that they are not created equals.
Available for commercial use, our patented Universal AV provides increased coverage and detection against known threats by using more than 10 anti-virus engines at a time while leveraging cloud technology for minimum performance impact.

Spark Connect delivers a simpler, secure and more efficient solution for your business collaboration.
Tier one, carrier grade networks delivering a broad spectrum of Voice and Internet, with market leading Cloud, Network and Security tools.
|
|
VISIT US ON LINKEDIN |
